BucketWars Writeup
Leveraging AWS S3 bucket versioning to leak files.
Challenge Description
We’re tasked with accessing a website that has an AWS S3 bucket and use its object versioning feature to retrieve files and eventually extract a hidden flag.
Solution
Step 1: Listing S3 Bucket Object Versions
By navigating on the website, we discover that the whole website leads us to the idea of versioning and that index-v1.html contains Yikes which hints that this is the entry point.
Thus, the first step was to list all available object versions in the S3 bucket using the AWS CLI. The following command was used to retrieve and store the output in a JSON file:
1
aws s3api list-object-versions --bucket bucketwars.ctf.csaw.io --no-sign-request --output json > out.txt
From the results, we discovered numerous files, but the two oldest versions of the file named index-v1 were of interest. To download the older versions I used the following commands:
1
aws s3api get-object --bucket bucketwars.ctf.csaw.io --key index_v1.html --version-id t6G6A20JCaF5nzz6KuJR6Pj1zePOLAdB index_v1_old.html --no-sign-request
1
aws s3api get-object --bucket bucketwars.ctf.csaw.io --key index_v1.html --version-id CFNz2JPIIJfRlNfnVx8a45jgh0J90KxS index_v1_old.html --no-sign-request
The first version contained the following image URL:
1
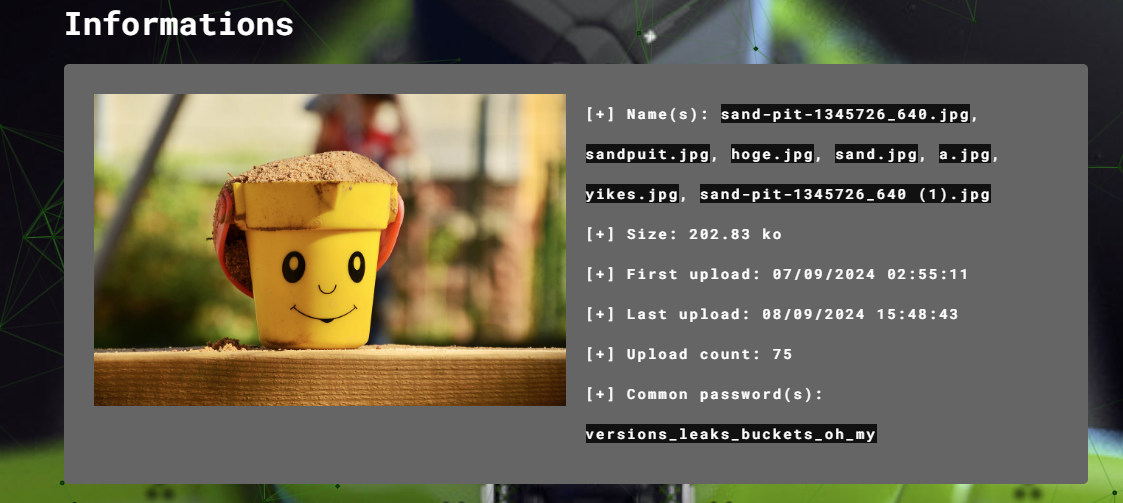
https://asdfaweofijaklfdjkldfsjfas.s3.us-east-2.amazonaws.com/sand-pit-1345726_640.jpg
The second version contained a comment:
1
<!-- Note to self: be sure to delete this password: versions_leaks_buckets_oh_my -->
This comment seemed to provide a clue — the password versions_leaks_buckets_oh_my.
Step 2: Investigating the Image
Next, we took the image URL from the first object version and uploaded it to Aperisolve, an online steganography tool. Interestingly, many users had already attempted to crack the image using the password provided in the comment. This gave us a strong indication that the password versions_leaks_buckets_oh_my was indeed meant for extracting hidden data from the image.
Step 3: Extracting the Hidden Data
Using the steganography tool steghide, we applied the password to the image:
1
steghide extract -sf sand-pit-1345726_640.jpg -p versions_leaks_buckets_oh_my
The command successfully revealed a hidden file named flag.txt. Opening this file provided us with the flag.
Flag
1
csawctf{lEaKY_Bu4K3tz_oH_m3_04_mY!}