Tracem 2 Writeup
Trace suspicious DNS requests to a user with spoofed MAC and figure out his AD username
Challenge Description
Another knock from our ISP and HR looking for a John Doe… but now it’s not so easy.
This challenge had 31 solves and 457 points.
Solution
Step 1: Useful Information
Based on Tracem 1, we know that:
- Our target made a request to an illicit website.
- Usernames can be found out from the Active Directory login logs by searching for
|xx.xx.xx.xx.
Step 2: Importing the logs into Kibana
I booted up a Kibana & Elasticsearch container on Docker based on this and imported the data
Some lines (the AD ones) could not be imported because they had too many fields, but it was irrelevant to my scope for Kibana.
Step 3: Finding illicit domains
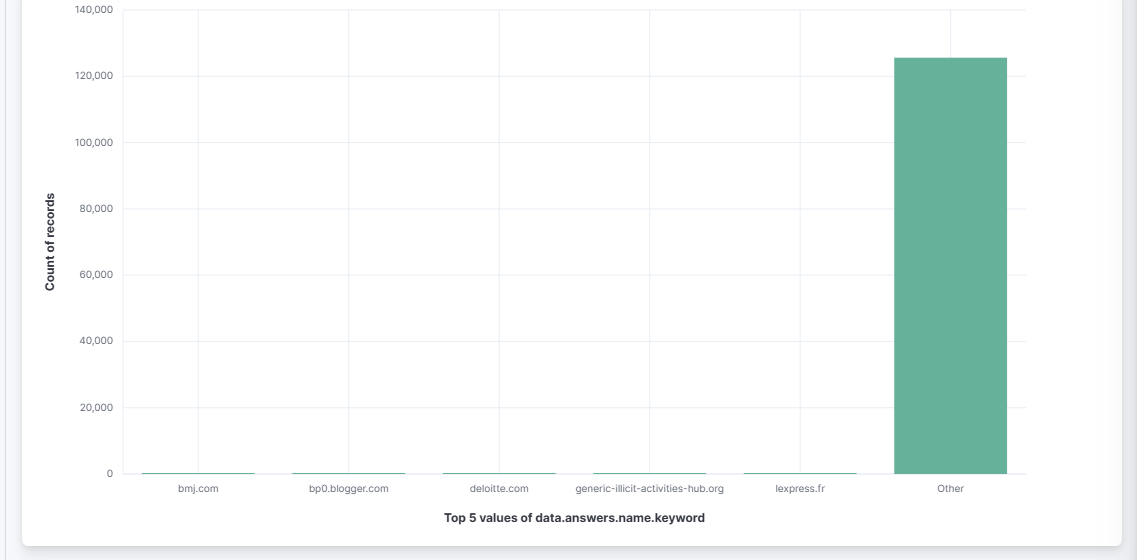
By visualizing the data.answers.name field and sorting it to be ascending instead of descending, we can find our first illegal domain, generic-illicit-activities-hub.org.
Step 4: Linking the accessed domain to our target’s IP
To make things easier, I switched on to VS Code and used Ctrl + F to navigate through the data. By searching for generic, we can find 4 entries, 2 queries to the DNS and 2 answers (1 for IPv4 and 1 for IPv6).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
{
"host": "primary",
"source": "stream:dns",
"sourcetype": "stream:dns",
"_time": "2024-12-04 09:05:01.76",
"data": {
"timestamp": "2024-12-04 09:05:01.197568",
"protocol_stack": "ip:udp:dns",
"transport": "udp",
"src_ip": "10.18.0.2",
"src_port": 53,
"dest_ip": "10.18.21.121",
"dest_port": 22066,
"transaction_id": 2835,
"answers": [
{
"type": "A",
"class": "IN",
"name": "generic-illicit-activities-hub.org",
"addr": "96.16.243.221"
}
]
}
}
Since this is an answer to the DNS query, the dest_ip field is the target’s IP, which is 10.18.21.121.
However, searching for |10.18.21.121 yields no results, which means that our target did not log in to the AD on this IP.
Step 5: Finding the MAC address
As we have no results for the AD for this IP, we will search for the MAC address of the target by finding his IP’s DHCP request.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
{
"host": "primary",
"source": "stream:dhcp",
"sourcetype": "stream:dhcp",
"_time": "2024-12-04 08:49:20.52",
"data": {
"timestamp": "2024-12-04 08:49:20.310176",
"protocol_stack": "ip:udp:dhcp",
"transport": "udp",
"src_mac": "de:ad:be:ef:ca:fe",
"src_ip": "0.0.0.0",
"src_port": 68,
"dest_mac": "FF:FF:FF:FF:FF:FF",
"dest_ip": "255.255.255.255",
"dest_port": 67,
"chaddr": "de:ad:be:ef:ca:fe",
"ciaddr": "0.0.0.0",
"transaction_id": 1005317175,
"opcode": "DHCPREQUEST",
"riaddr": "10.18.21.121"
}
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
{
"host": "primary",
"source": "stream:dhcp",
"sourcetype": "stream:dhcp",
"_time": "2024-12-04 08:49:21.00",
"data": {
"timestamp": "2024-12-04 08:49:20.982612",
"protocol_stack": "ip:udp:dhcp",
"transport": "udp",
"src_mac": "EB:A8:B3:FB:A0:AB",
"src_ip": "10.18.0.2",
"src_port": 67,
"dest_mac": "de:ad:be:ef:ca:fe",
"dest_ip": "10.18.21.121",
"dest_port": 68,
"chaddr": "de:ad:be:ef:ca:fe",
"ciaddr": "10.18.21.121",
"transaction_id": 1005317175,
"opcode": "DHCPACK"
}
}
This is where our target was assigned his IP address, and we can identify that his MAC address is de:ad:be:ef:ca:fe. This technique, known as MAC spoofing, involves changing the MAC address of your device.
Following the trail, we can find the DHCPRELEASE
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
{
"host": "primary",
"source": "stream:dhcp",
"sourcetype": "stream:dhcp",
"_time": "2024-12-04 09:22:01.12",
"data": {
"timestamp": "2024-12-04 09:22:00.411200",
"protocol_stack": "ip:udp:dhcp",
"transport": "udp",
"src_mac": "de:ad:be:ef:ca:fe",
"src_ip": "10.18.21.121",
"src_port": 68,
"dest_mac": "FF:FF:FF:FF:FF:FF",
"dest_ip": "255.255.255.255",
"dest_port": 67,
"chaddr": "de:ad:be:ef:ca:fe",
"ciaddr": "0.0.0.0",
"transaction_id": 2674233379,
"opcode": "DHCPRELEASE"
}
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
{
"host": "primary",
"source": "stream:dhcp",
"sourcetype": "stream:dhcp",
"_time": "2024-12-04 09:22:01.15",
"data": {
"timestamp": "2024-12-04 09:22:00.519792",
"protocol_stack": "ip:udp:dhcp",
"transport": "udp",
"src_mac": "EB:A8:B3:FB:A0:AB",
"src_ip": "10.18.0.2",
"src_port": 67,
"dest_mac": "de:ad:be:ef:ca:fe",
"dest_ip": "10.18.21.121",
"dest_port": 68,
"chaddr": "de:ad:be:ef:ca:fe",
"ciaddr": "10.18.21.121",
"transaction_id": 2674233379,
"opcode": "DHCPACK"
}
}
This unfortunately means that we have reached a dead end, as the target only had one IP address associated with his MAC address and no corresponding AD logins.
Step 6: Identifying the real target
If you search for MAC spoofing, you’ll find that it is often used to impersonate another user. This gave me an idea: we have all DHCP requests, both DHCPREQUEST and DHCPRELEASE, so we can track all IP addresses assigned to each MAC address. If a user was impersonated, we would see two successive DHCPREQUEST entries without a DHCPRELEASE in between, indicating that two IP addresses were assigned simultaneously to the same MAC address.
Step 7: Finding the impersonated user
I generated and fine-tuned a JS script to monitor all DHCP requests to find the MAC Spoofing and it quickly yielded results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
const fs = require('fs');
fs.readFile('logs.json', 'utf8', (err, data) => {
const lines = data.split('\n');const macRequests = {};const macReleases = {};const result = [];
lines.forEach(line => {
const log = JSON.parse(line);
const macAddress = log.data.chaddr;
const timestamp = log.data.timestamp;
const requestedIp = log.data.riaddr;
const currentIp = log.data.ciaddr;
const opcode = log.data.opcode;
if (opcode === 'DHCPREQUEST') {
if (!macRequests[macAddress]) {
macRequests[macAddress] = [];
}
macRequests[macAddress].push({ requested_ip: requestedIp, timestamp: timestamp });
}
if (opcode === 'DHCPRELEASE') {
if (!macReleases[macAddress]) {
macReleases[macAddress] = [];
}
macReleases[macAddress].push({ released_ip: currentIp, timestamp: timestamp });
}
});
for (const mac in macRequests) {
if (macRequests[mac].length > 1) {
for (let i = 1; i < macRequests[mac].length; i++) {
const firstRequest = macRequests[mac][i - 1];
const secondRequest = macRequests[mac][i];
if (firstRequest.requested_ip !== secondRequest.requested_ip) {
const releases = macReleases[mac] || [];
const releasedIps = releases.map(r => r.released_ip);
if (!releasedIps.includes(firstRequest.requested_ip)) {
result.push(`Potential spoofing detected for MAC: ${mac}. IPs requested: ${firstRequest.requested_ip} and ${secondRequest.requested_ip}`);
}
}
}
}
}
console.log(result)
});
1
2
Potential spoofing detected for MAC: 53:75:56:a7:98:8f. IPs requested: 10.17.161.10 and 10.18.13.187
Potential spoofing detected for MAC: 53:75:56:a7:98:8f. IPs requested: 10.18.13.187 and 10.17.161.10
This means that we had two IPs simultaneously assigned to 53:75:56:a7:98:8f. Therefore, one of these two IPs is our target’s real IP.
By taking the first one, 10.17.161.10, and searching with |10.17.161.10, we find the following log (shortened for brevity):
1
2
3
4
5
6
7
8
9
{
"host": "primary",
"source": "udp:514",
"sourcetype": "syslog",
"_time": "2024-12-04 07:42:16.11",
"data": {
"_raw": "2024-12-04 07:42:16.058355||https://sso.evil-insurance.corp/idp/profile/SAML2/Redirect/SSO|/idp/profile/SAML2/Redirect/SSO|6be5e0fe638be3ae75c3702ae6f3fa91|authn/MFA|10.17.161.10|Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Firefox/53.0.3 Safari/537.3|https://sso.evil-insurance.corp/ns/profiles/saml2/sso/browser|mhammond||uid|gitlab......"
}
}
Our target IP 10.17.161.10 logged on with user mhammond.
Submitting the flag as irisctf{mhammond} worked, which proves that our approach was correct.
Conclusion
To summarize the steps we took:
Analyzed Previous Challenge Information: We used insights from Tracem 1 to understand that the target made a request to an illicit website and that usernames could be found in Active Directory login logs.
Imported Logs into Kibana: We set up a Kibana & Elasticsearch container to visualize and analyze the logs.
Identified Illicit Domains: By sorting the
data.answers.namefield in Kibana, we identified the illicit domain accessed by the target.Linked Domain to Target’s IP: We used VS Code to search through the data and found the target’s IP address from the DNS query responses.
Found the MAC Address: We searched for DHCP requests to find the MAC address associated with the target’s IP, revealing that the target used MAC spoofing.
Identified the Real Target: We hypothesized that MAC spoofing was used to impersonate another user and wrote a script to detect potential spoofing by finding successive DHCP requests without releases.
Found the Impersonated User: The script identified a MAC address with two IPs simultaneously. We searched for one of these IPs in the AD logs and found the real target’s username.
By following these steps, we successfully traced the suspicious DNS requests to the user with a spoofed MAC address and identified his AD username.
Flag
irisctf{mhammond}